Certain incidents of email phishing attacks targeting the users of kerala.gov.in mail domain has been noticed. The email pretending to be from NIC (kerala.gov.in@nic.in), asks the user to confirm and verify the ownership of the account. The email contains a confirmation link to one of the spoofed websites, which tries to steals the user’s login credentials. The screenshot of the same is attached for your kind reference.
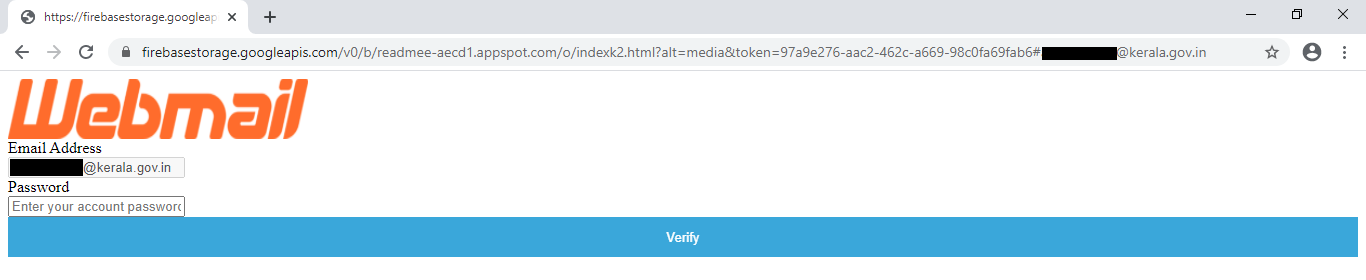
Further, the phished email accounts are then used to send malwares to other sensitive Government organizations and users. These mails contain topical and context-aware contents to lure the targets into opening the malicious attachment, thus infecting their system. The malware can then create persistence inside the targeted organization's network, and be used for various malicious activities such as stealing sensitive data.
The following pretext is the content of fraudulent phishing mail which seems to originate from NIC:
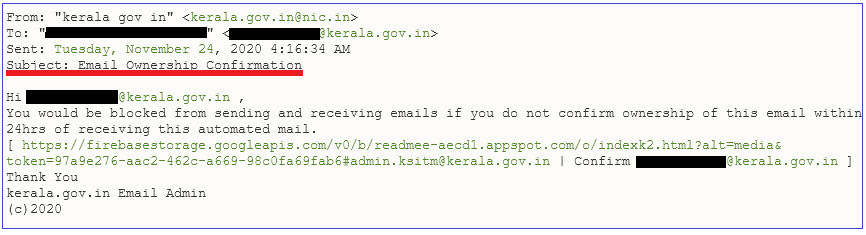
You are advised to kindly take the following preventive measures to protect your computer networks and information from this type of similar attacks:
- Do not open attachments in unsolicited e-mails, even if they come from people in your contact list. Never click on a URL contained in an unsolicited e-mail, even if the link seems genuine.
- Always ensure that the URL in the address bar is exactly https://email.gov.in whenever you are entering your credentials for the website. Ensure that no other characters (hyphen, numerals etc.) are present in the URL.
- Beware of emails that greet you impersonally, such as 'Hi following <Email ID'> or 'Dear Friend'. Real organizations greet by the name of the recipient in their mails start with a salutation like 'Dear Mr. <Name of the recipient>'. Besides impersonal greetings, phishing mails may often contain spelling and grammatical errors that reputed organizations would not make.
- Phishing emails often copy the entire look of a legitimate emails, making it appear authentic. Even if email comes from a legitimate organization requesting personal financial/sensitive information, to be safe, first make a call to the legitimate organization to see if they really sent that email.
- Check the integrity of URLs before providing login credentials or clicking a link. Do not submit personal information to unknown and unfamiliar websites.
- Never submit confidential information via forms embedded within email messages. Senders are often able to track all information entered.
- In cases of genuine URLs, close the e-mail and go to the organization's website directly through browser's address bar.
- Inform the security team of the organization, if any suspicious mails, files etc. are received.
- Beware of emails and Web Pages providing special offers like winning prize, rewards, cash back offers etc.
- Install antivirus software and keep it up to date, will help detect and disable malicious software.
- Update spam filters with latest spam mail contents.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
Note:
Any unusual activity or attack should be reported immediately at incident@cert-in.org.in, cert.ksitm@kerala.gov.in with the relevant logs, email headers etc. for analysis and taking further appropriate actions.
